Quick Answer:
Yes, but only when you need it.
Long Answer: You want to learn about this in depth
VPN’s are both a simple and complex technology. The tech itself is pretty simple but the implementation is complex.
What does a VPN do?
VPNs encrypt your traffic from 1 location to another location. This means depending on your goals your traffic can be inspected on your local machine and the end of the tunnel.
What do they not do?
Protect your privacy. Only you can protect your privacy through good internet hygiene. VPNs can help with this but if you login to your facebook while on VPN, well that’s not private, and you now tied your identity to that IP address.
How do VPNs work?
The way computers talk to each other is through a number of different protocols and mechanisms. You will learn here in depth how VPN’s accomplish their goal, and how they can be implemented differently.
There are 7 layers in the OSI model (they guide on building communications with computers)
- The hardware Layer. This is your wifi router or ethernet cable.
- The data link layer. This is how information is sent down the wire. It’s network packets.
- The IP Layer: This is the different ways packets can be formed to sent information. IP addresses behave here.
These are the layers you need to know to understand how VPNs work.
In all computing computers have three main protocols to establish connections:
- ARP
- TCP/UDP
- Routing Tables
All computers have MAC addresses (not apple computers, Machine Address Code) This is a unique address that no other devices in the network should have, and it’s tied to the hardware (not always) of the network adapter. The network adapter handles Layer 1. Mac addresses are Layer 2.
ARP
On Layer 2:
ARP is Address Resolution Protocol. When 1 computer wants to talk to another, it asks for the IP address for a MAC so it knows who to talk to. It sends an ARP request to the broadcast address for a subnet (you don’t need to know what that is, just know it sends the request to everyone it can). When a computer that has the IP recieves a request it sends the response to that computer. ARP has allowed these computers to find each other.
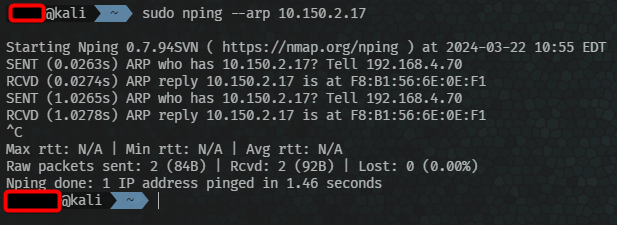
TCP/UDP
On Layer 3:
This is the protocol by which computers establish “sessions”. Once two computers know where each other are. how can they talk? how do they know what language to talk? TCP (Transport Control Protocol) is a “handshake” to allow both computers to negotiate how to talk. This is through 3 packets SYN, SYNACK, ACK.
Computer 1 > SYN > Computer 2 (Hey, can you talk?)
Computer 1 < SYNACK < Computer 2 (Hi, yes, I can talk, Are you ready to talk?)
Computer 1 < ACK < Computer 2 (Hi, yes, I am ready to talk)
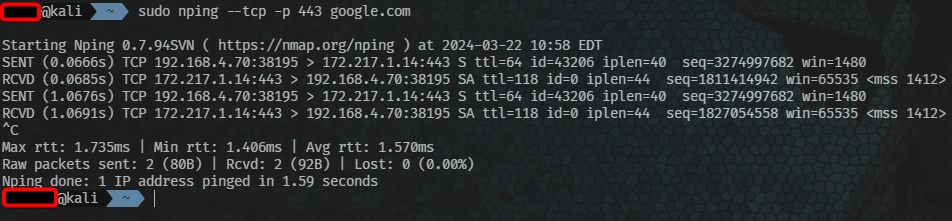
! NOTE: This image doesn’t show the final ACK in the negotiation, the command I put doesn’t send a final ACK.
This means the computers are ready to speak and a session has been established. Now they just need a protocol to speak, this can be anything, like http (web traffic), dns (name to IP translation), smb (file transfers), etc.
Routing Tables
On Layers 1,2:
Your computer needs to have configured some things in order to work. Most of the time a protocol called DHCP is used to automatically configure this but it can be done manually as well.
- Subnet mask - You don’t need to know what this is, but it is the range of IP addresses on your computer’s local network. typically it looks like 192.168.1.0/24 or 255.255.255.0
- Default Route - This is how your computer talks to everything. usually looks like 0.0.0.0/0 (This says all traffic goes here so it can be routed) your default route almost always goes to 192.168.1.1
- IP address - This is your address. usually given to you but you can say what your IP is. it’s usually 192.168.1.X (anything between 2 and 254 where the X is.)
You will always have 2 routes on your machine. The first to the default gateway and the second for your local network. This is so you can talk on your local network and the internet simultaneously.
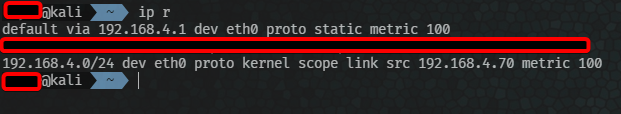
To summarize, if I want to open google.com in a browser this happens.
- My computer needs the IP for Google. So I make a dns request to my dns provider (this is almost always your ISP unless you changed it) Your DNS provider will then give you the IP assuming they found it themselves.
- Now that I have the IP I need to find the computer I want to talk to This is where I will check my routing table and find the router needs to route it over the internet.
- Since I know who to send the information to now, I can send all my packets over TCP/UDP to the IP address I want to talk to, which is google’s servers, and I can use the google.com name.
- My computer sends the http traffic to my router and includes the information the router needs to send to the correct place (google’s IP in this instance)
How do VPN’s change this?
Simply put, on Layer 1 hardware is emulated with a custom network adapter. Your computer will be configured in 1 of 2 situations.
-
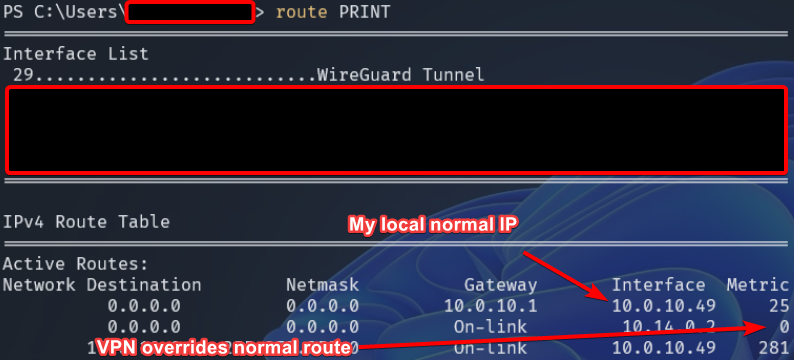
Split tunneling - Your VPN will add an additional entry to your routing table and send packets to that VPN. This is useful when only some IP addresses need to go down the VPN. Usually used in business work from home environments.
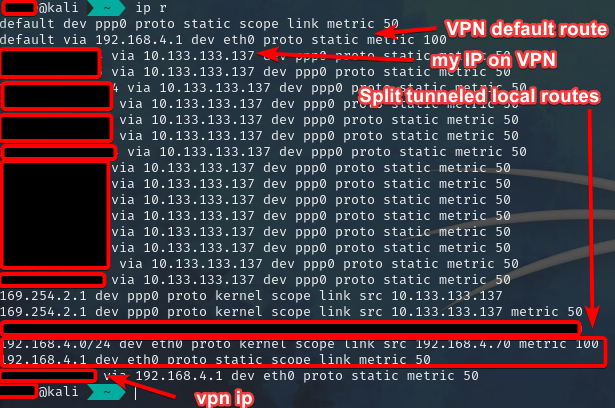
-
ALL VPN - your VPN will replace your default gateway and route packets through itself to your existing gateway. (gateway is another way of saying default route). This is going to send EVERYTHING above layer 1 through the VPN.
So when should I use a VPN and when should I use a proxy?
If you want to encrypt and send all your traffic to a place your ISP, Government, etc can’t inspect, use a VPN. Without split tunneling configured, you will have full protection from spying eyes up until the packets leave the VPN tunnel. Meaning your VPN provider needs to be one you trust.
If you only care about your HTTP traffic, use a proxy. Your proxy will not encrypt your traffic in most instances, you will need to rely on HTTPS (TLS) on all the websites you go to.
So what do I recommend?
- Don’t use a free VPN.
- Use one that have been vetted
ExpressVPN used to be good. It is not anymore
NordVPN has had breaches in the past
I personally use surfshark, I don’t recommend it but it accomplishes my goals
Why not a proxy?
If you know the following, you can use a proxy with equal effectiveness
- How to modify your routing table
- How to kill your internet if your proxy disconnects
- You know how to correctly configure DNS over HTTPS so cert failures don’t allow MITM attacks
- You know what WEBRTC is and how to prevent WEBRTC revealing attacks
- You’re not concerned with client side javascript in a webpage revealing your real IP using ICMP or another protocol.
- You’re a network engineer and know all the other things Ive missed.